Intelligent Theft Detection System for Power Utilities

Across many cities, electricity poles are the most vulnerable points in the entire power network. Late at night, illegal wires are quietly hooked to live lines. Meters are tampered with. Connections are bypassed. A single pole-level theft can overload transformers, cause sudden outages, damage appliances, and leave honest customers paying the price. And for power utility teams, finding these hidden theft points is extremely difficult as it takes hours of manual patrolling, guesswork, and field visits.
Our next-generation AI-powered platform helps electricity boards automatically spot, track, and prevent power theft. It watches how electricity is flowing across poles, meters, and feeders, and immediately alerts the team when something looks suspicious. Whether it's a sudden surge, a drop in consumption, or an unusual connection pattern, our smart solution picks it up instantly.
How Power Theft Usually Happens


Illegal hooking from poles.


Bypassing or tampering with meters.
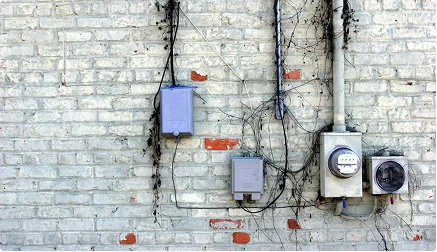

Unregistered connections pulled directly from live wires.


Laod manipulation by small shops, homes, or industries.


Sharing or splitting one legal connection into multiple illegal ones.
Product Overview
This is a comprehensive, automated theft detection engine that continuously evaluates:
Theft Identification
Sudden changes in electricity usage
Unusual load on a pole or transformer
Areas receiving more power than what is billed
Meters showing abnormal or repeated patterns
Connections drawing power even when meters show zero usage
Comparison of supply vs. actual consumption in an area
Key Features
- Instant warnings when the system detects unusual activity.
- Shows red zones on a map where theft is happening frequently.
- Learns from past theft incidents and improves accuracy over time.
- Works with existing smart meters, feeders, and utilities’ control rooms.
- Provides the exact location and suspected method of theft to speed up inspections.
- Helps utilities understand which areas face repeated theft, the time patterns when it happens most, and where preventive action is needed.
Impact
Up to 30-50% reduction in theft related losses

Faster identification of problem

Fewer outages caused by illegal tapping

Improved billing accuracy
Benefits
Find theft locations quickly
Reduce power losses and improve revenue
Lower the burden on field teams
Improve supply quality for honest customers
Prevent transformer overloads and outages
Strengthen trust between utilities and consumers
Data Security & Compliance

Utility-grade cybersecurity
End-to-end encrypted data transfer
Robust access control and audit logs
Compliant with Indian electricity board regulations
Robust access control and audit logs
End-to-end encrypted data transfer

Utility-grade cybersecurity
Compliant with Indian electricity board regulations
Why Choose Us ?
Strong
experience in
AI-driven
infrastructure
monitoring
Proven results in
government and
utility
deployments
Customizable
algorithms for
Indian
distribution
networks
Dedicated
implementation
and on-ground
support
Rapid
deployment with
minimal system
overhaul
Stop Power Loss Before It Escalates.
Detect electricity theft early, protect revenue, and strengthen grid reliability with AI-driven monitoring.
Connect With UsI am Nexus.









